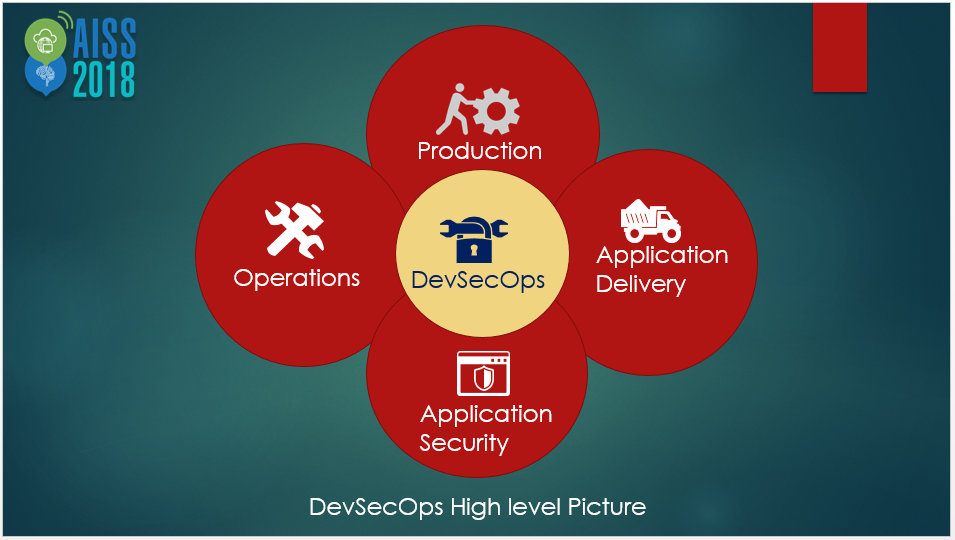
DevSecOps – Seamless integration of application security into Software development lifecycle
The driving concept behind DevSecOps is, empowering a software development process without sacrificing the security of the application and allow security decisions to be made quickly so as not to stifle productivity. In every business environment, DevOps as a concept is being embraced heavily. Application developers alongside operation engineers have started being agile in their approach for software development and deployment.
Power of DevSecOps
- Secure Coding – Security on the go
The concept of Security-as-Code – is one of the fundamental tenets of DevSecOps allowing developers to securely define infrastructure with programming language and deploy it in an automated fashion.
For example, if you are a developer, you can define what security groups you would like to create, combined with the services you wish to expose or you could also write automated checks using security tools such as NMAP/Wireshark which will scan to see, what ports are open and will fail.
Before the recent focus on agile practices and automated testing, developers had the tendency to write code without testing it by themselves. It was more common to handover the code to a quality assurance team and let them find the bugs. Now, secure coding and automated testing turned to be key enablers for DevOps movement, makes it easy to find and fix bugs more quickly; and fewer bugs make it to production.
Security should be no different. Security is part of quality and should be tested just like functionality.
A developer should think of security while development is in progress. This is done by writing security test cases that validate that your software is secure in an automated fashion from the beginning.
Let’s consider the following practical example.
In REST API that requires authentication, you create tests that ensure no restricted URLs can be hit without proper authentication.
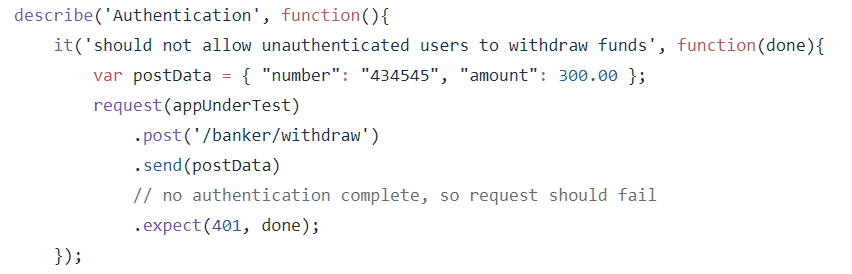
Here, test in a Node.js REST API that makes sure that a 401 HTTP code is returned when an authentication token is not sent with the request. If this code fails, then there will be a major problem with authentication. The learning here is, if developers run tests during development, they can ensure that the basic security requirements of system are covered.
- Smart Integration
Identifying security vulnerabilities, potential threats and risk associated with it requires collaboration between all the different elements and people that ultimately bring a new product or service to the fore. It doesn’t mean that single person should be a master of all these skills, but it’s useful to have an understanding of them.
For example, Operations engineer working with a developer to identify a security vulnerability in their application, and likewise, a developer working closely with an operations engineer.
- Application Vulnerability Correlation
To identify vulnerabilities in application stack from various tools, you triage flaws to make sure that there are no false positives. Automatic correlation of vulnerabilities, intelligently allows you to correlate common vulnerabilities based on CWE (Common Weakness Enumeration) value and gives more relevant and focused results. This helps to identify and mitigate security issues faster. Most of the intelligent correlation engines figure out vulnerabilities by themselves and place those in the right category.
- Proactive Analysis
Effective way that can transform a DevOps engineer to DevSecOps engineer is ‘by proactively thinking about security when monitoring systems which are into production’. To start with, developers can build checkpoints in monitoring plan to monitor systems for important security updates and regular alert for patching. SIEM could be leveraged to monitor application logs and generate alerts on failed login attempts, patterns matching DoS/DDoS-based attacks, and many more.
- Automated Toolchain
Using effective and relevant tools when thinking about security is crucial. Integration of tools and techniques allow to set thresholds for security and compliance, including PCI, CIS Benchmarks, and do this within the build itself. It’s a good strategy for application security teams to automate manual testing results and also perform manual penetration tests on your applications as usual. While testing, also document interesting and complex exploits that are found and transform these manual tests into automated scripts.
The importance of DevSecOps can’t be unnoticed. As nefarious individuals become more active at finding vulnerabilities in software and hardware, so must developers adapt to the changing landscape. We need to be agile in our approach towards security and act collectively in addressing the issues, so that we will be able to reduce the attack footprint on applications and services. This gives us a a better understanding of security in the extreme age of digitization.
Join us at Annual Information Security Summit to explore more on this topic and other relevant developments in emerging technologies which will shape the future of Cyber Security. Register Now https://aiss2018.dsci.in/