Going by the recent media reports, it would seem that the malicious hacker groups behind data breaches are in a competition of sorts. The latest Equifax data breach, which exposed the records of 143 million American citizens, is a case in point. The following table presents a snapshot of some of the biggest data breaches till date:
| Sl. No. | Target Company | Number of affected accounts |
| 1. | Yahoo | 500 million |
| 2. | MySpace | 360 million |
| 3. | Equifax | 143 million |
| 4. | > 100 million | |
| 5. | Target | 40 million |
A common theme among these attacks is that they were targeted, conducted over an extended period of time and identified much later. Some of these attacks date back to 2012, yet this has become a common occurrence these days. This raises certain questions. Are companies not doing all that they should to protect their customer data? What lessons have they learnt from their peers who were breached? Why are they waiting to be targeted before implementing these lessons? Or is it that they have resigned their fate in the hands of malicious hackers?
Earlier this year, it became evident that targeted attacks is just one of the threats that companies face. Massive global cyber-attacks, such as WannaCry and NotPetya / Petwrap ransomware, demonstrated how companies can be affected by cyber-attacks without even being in the direct crosshairs of the perpetrator. Take for instance the impact of WannaCry. It hit more than two lakh machines, in 150 nations. Most of the affected companies had to halt their operations to contain the ransomware infection within their network. Some of the sectors affected by WannaCry were Health Services, Automobile Manufacturers, Telecom Services Providers, Banks, Logistics, OEMs, and Railways.
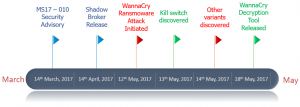
If one were to analyse the timeline of WannaCry (as shown below), or even PetWrap for that matter, one would observe that majority of affected companies failed to implement the MS17-010 security patch. This patch was released by Microsoft two to three months prior to these attacks.
Apart from patch management, following are key security parameters which got tested during these attacks:
- Zero-days, play of state actors
- Disclosure of vulnerability by technology providers
- Security ramification of unsupported operating versions
- Perpetration of the attacks
- Ability to estimate possible damage to assets
- Swift isolation of damages
- Security operations, threat & vulnerability management
- Backup and recovery preparedness
- Incident/ Breach response preparedness & maturity
- Information sharing & its productivity for swift response
- Collaboration with external entities
- Role of national security agencies & catalyst forces- working with them
If anything, these attacks should serve as a wake-up call to organizations, both big and small, to get their basic cyber security practices right. They should perform a deep introspection of their security practices to begin with. With nation-state actors leveraging the cyberspace for their own interests, cyber security is no longer just an enterprise issue. It has now transformed into a political issue and organizations should start treating it as such.
Join us at DSCI-NASSCOM Annual Information Security Summit (AISS) 2017 for an extensive discussion on Potent & Wider Attacks. To know more about AISS 2017 and registration visit https://www.dsci.in/aiss-2017/
To stay updated on latest cyber threats participate in DSCI Threat Intelligence & Research (Ti&R) initiative. To participate drop us a mail at tir@dsci.in
