Why monitor?
According to a Q4 2021 Internet security report from WatchGuard, almost 66% of all threats were zero-day vulnerabilities. Another statistic from Mandiant Threat Intelligence report states about 40% of threats from the entire decade occurred in 2021 alone. The trend is not just alarming but clearly points to one definite thing – monitoring is a MUST. Despite every organization best ability to defend itself against known threats, it would be very challenging, if not impossible to defend against zero-day vulnerabilities.
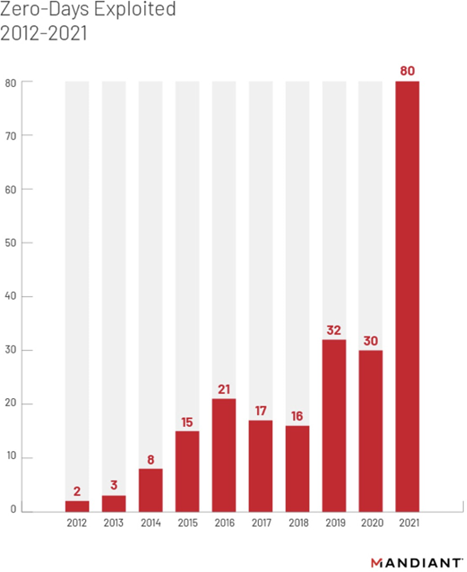
If you are wondering how continuous monitoring might help in this situation, let me explain. The ability to defend against an unknown threat and respond quickly to some vicious event are two distinct and completely different possibilities. Monitoring helps in the latter.
Worldwide, regulators are tightening the laws around security incidents and data breaches. While the EU has stipulated a maximum of 72 hours for data breach, the USA has several state laws and in India the CERT-In has mandated a tiny 6 hour window to cover the same. While we cannot ascertain the exact nature of futuristic laws related to cybersecurity, the direction is fairly obvious that companies would be required to be far more vigilant and respond faster.
In summary, to possibly detect newer threats, to be compliant and provide confidence about your company and brand to customers, you need to monitor and that is no longer an optional operation for companies across the globe.
Definitions
Before we jump in to the various solutions available in the market and analyze them in detail, let us make sure we are aligned with respect to the definitions used in this article. The industry, largely, uses the same terminologies but a disclaimer worth mentioning is that there can be minor discrepancies, depending on whom you are talking to.
Security Incident and Event Management (SIEM), typically an off-the-shelf software that offers real-time monitoring and cross-correlation of events from multiple sources. In other words, ideally it should help your organization in recognizing potential threats before they occur or at the least help you respond quickly and isolate assets and mitigate the threat.
SIEMaaS refers to the offering where the same piece of software discussed above is being fully managed by a vendor, which means upgrades, patches, pre-existing automated integration with ticketing systems are part of the service.
Security Operation Center-as-a-Service (SOCaaS) is a complete infrastructure where people, technology and process is driven by the service provider. Customers agree to SLAs on threat detection, handling and response. All relevant logs are “ingested” into the SOC and the customer pays the service provider, usually on the basis of events generated or in a few cases, the number of devices monitored.
Managed Detection and Response (MDR) is again a managed service but not just monitoring and alerting customers about possible incident/intrusion. The most defining and important distinction is that it also includes “a response”, which means that the customer believes the vendor has sufficient knowledge, skills and responsibility to handle responses or take remediative actions.
SIEM
SIEM is a software most useful to organizations that have ready capabilities in terms of skillsets to manage the software and integrate with your internal ticketing system. Besides capabilities, you would also have to account for the time spent on “maintenance” of the said software and any additional tweaks that might be required to the integrations with other software.
SIEMaaS
If your organization has limited resources to maintain a SIEM but has sufficient understanding of which software you want to use, SIEMaaS is the BEST option. Often, this is also referred to as “Managed SIEM” where the vendor takes care of running the infrastructure for you.
SOCaaS
What the earlier solutions were not providing is the visibility to threats on a real time basis. The integrations with your ticketing systems, were the lifeline. Also, remember that you will be alerted only on scenarios you had programmed for!! That leaves a big gap in terms of uncovered possibilities. Additionally, most SOCaaS providers have the following limitations with respect more advances solutions like SOAR, integrations with multiple threat exchanges and advanced remediation options.
MDR
Of the lot, this is the most advanced solution which can collect & correlate, detect & respond not just to a limited set of scenarios defined in the playbook but to newer and dynamic threats. In some cases, depending on how and where the solution is deployed, log ingestion might not be necessary and still MDR can detect and block external threats.
In most cases, MDR solutions would be actively listening to several IOCs (Indicators of Compromise) from multiple threat intelligence exchanges / sources. Clearly, this would be quite an expensive solution.
Key factors that influence decision-making :
Still confused? No surprises if you are unable to makeup your mind about the right level of service required for your organization merely based on the basic explanation of what they are. There are some key factors that can potentially influence your decision on arriving at your choice and they are listed below:
◎ Organziation’s capability and maturity level
The range of skillsets readily available within the company to handle software related to incident management and maintaining them on a regular basis will certainly be a factor that influences which solution you can or cannot choose. Apart from the availability of appropriately skilled people, they should have sufficient time bandwidth to handle these tasks.
◎ Existing systems that need integration
The number of logs (devices, network, applications, identity and several others) might need to be first identified as a source and later ingested into the system. How effectively, the solution handles the broad spectrum of logs and detects potential threats is a key consideration. Also, if escalated events need to be propagated to appropriate people in the company or just log a ticket, needs integration with 3rd party systems. The availability and completeness of this integration is also another key factor.
◎ Infrastructure Complexity
The number of devices or endpoints, routers, gateways, cloud resources are some of the several resources a company could list as its infrastructure assets. The larger the number of assets, the larger the number of events generated by them. The larger the events generated, the complexity increases exponentially. Correlation needs to occur across endpoint devices, network devices, authentication/authorization of users from unknown devices / locations / networks and several other sources. The solution chosen should have the capability to handle such an amount of load seamlessly and also provide the ability to react quickly. In other words, if the processing and correlation time is too high, an incident and worse an incursion could have already occurred.
◎ Cost
Last but certainly not the least, every solution has a price-point. Solutions chosen or shortlisted definitely need to take into account the available budget. Typically, the SIEM will have a monthly/annual recurring fee, just like any other SaaS product, the SIEMaaS will depend on which SIEM was chosen and the extent of services taken. SOCaaS, on the other hand, relies heavily on the events generated and to some extent the number of devices.
One important administrative aspect less spoken about is that SIEM and SOCaaS can be looked at largely as a compliance solution whereas MDR is mostly around threat management. Based on all these factors, you should be able to arrive at a decision quickly.
The following table might be of some help in presenting the above details in an easy to read format.
| Feature | SIEM | SIEMaaS | SOCaaS | MDR |
| Logs collection & event correlation | Yes | Yes | Yes | Maybe |
| Infrastructure complexity | Low | Low | Medium to High | Very High |
| Integration with internal systems | Very high | Medium | Low | Low or NIL |
| Threat intelligence | NIL to Minimal | NIL to Minimal | Medium | Very high |
| Cost | Low | Low | Medium | High |
Simplifying the above table, a start-up would typically go for SIEMaaS or SIEM, depending on whether in-house resources are available. Medium to large corporations are likely to choose MDR as an additional layer of defense to protect from various external threats on a continuous basis. A medium sized organization with about 1000 employees is likely to choose SOCaaS to balance cost and compliance / threat management.
About the author–
Ramakrishnan Seshagiri is the Managing Director of CyberSafeHaven Consulting, a boutique cybersecurity consulting that specializes in application security, DevSecOps and VAPT services, a company that has developed a proprietary threat modelling framework and pioneered the concept of appsec plans. He is enlisted as a Scholar in the National Security Database, completed Advanced Cyber Security Programme from Stanford University and holds a post graduate diploma from NLSIU, Bangalore. He also holds the following security certifications: CISSP, CISM, CCSP, and AWS-Security Specialty.
